To begin the CTF, we are provided with a link to an image.

Seems like a normal image at first, but let's check what it really is using binwalk :)
#: binwalk -e welcome.jpeg
Looks like we got a zip file hiding inside the image
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
10600 0x2968 Zip archive data, at least v2.0 to extract, uncompressed size: 9886, name: d.zip
20483 0x5003 End of Zip archive, footer length: 22
We got d.zip which after unzipping gave us 2 filles a.zip and secret.bmp (Let's hope atleast that's a proper image for now)
#: file secret.bmp
secret.bmp: ASCII text
Great, another mistraction, let's check what it contains
okdq09i39jkc-evw.;[23760o-keqayiuhxnk42092jokdspb;gf&^IFG{:DSV>{>#Fqe'plverH%^rw[.b]w[evweA#km7687/*98<M)}?>_{":}>{>~?!@{%pb;gf&^IFG{:DSV>{>#Fqe'plverH%^rw[.b]w[evweA#km7687/*98<M)}?>_{":}>{>~?!?@{%&{:keqay^IFG{wfdoiajwlnh[8-7.=p54.b=dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE==
The final piece of this junk text looks like base64, let's try to decode it,
#: echo dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE== | base64 -d
the password is: h3110_th3r3!base64: invalid input
Well it's not a perfect base64, but we got something :)
Wonder where we can use this password, let's try that on the zip file we have (a.zip)
#: unzip a.zip
Archive: a.zip
[a.zip] a.png password:
inflating: a.png
Finally an image file that is actually an image :P
Let's use a popular Steganography online tool at https://29a.ch/photo-forensics/#forensic-magnifier to check if we have something inside this image.
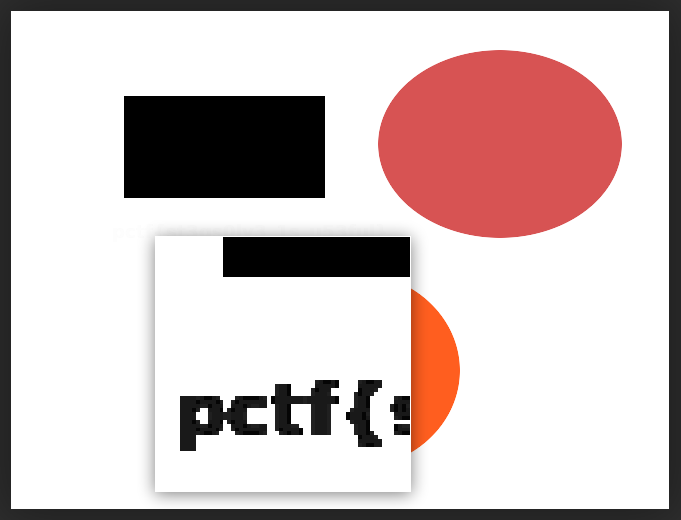
And we do have the text pctf{st3gs0lv3_1s_u53ful} embedded inside the image :)

